Reputational damage, loss of revenue, and a sustained impact on the bottom line can all result from a notable data breach.
In 2021, an HSE employee opened a phishing email attachment that caused a ransomware attack on Ireland’s national health service, resulting in over €100 million in remedial costs. In the same year, a study released by Flashpoint and Risk Based Security found that a previously optimistic drop in the total number of breaches was likely incorrect, and instead only appeared to be reduced due to the highest increase since 2014 in the time it takes for an organization to report a breach.
Clearly, data breaches are a huge risk, and currently, many businesses are not suitably prepared to avoid them or deal with their aftermath. To learn how to prevent a data breach in your business, read on for seven key practices to adopt.
TRENDING
Closing the Data Risk Gap
Find out what data privacy and compliance professionals consider to be the #1 risk to the business in 2022.

Download your guide now
1. Multi-factor authentication
The importance of using strong passwords is understood by most, but password strength alone cannot always guarantee security. To increase login security, organizations should use Multi-Factor Authentication wherever possible. This is sometimes referred to as 2-Factor Authentication, whereby an individual logs in using a strong password, and then is required to provide a confirmation code sent via email or mobile app.
This security feature ensures that, even if an employee’s password is compromised, the hacker would also need to gain access to a personal device or separate account to achieve login access. This is a simple and easy way to help guarantee sensitive data is kept private and secure.
2. A risk-based approach
A risk-based approach to avoiding breaches normally involves a systematic method that identifies, evaluates, and prioritizes threats facing an organization’s cyber and data security. This is an essential step in avoiding data breaches as, once you know where the risk is, you can take appropriate action to mitigate or avoid it.
Conducting thorough risk assessments can help to identify where your organization needs to improve, and where you need to invest in further security measures. Self-service risk assessments can also quantify how much further training is required and for which teams.
3. Thorough training
How do data breaches happen? Unfortunately, people make mistakes and can be caught out by sophisticated phishing techniques. According to Verizon’s Data Breach Investigations Report, 85% of data breaches in 2021 were due to the “human element.” However, with appropriate training, teams can be taught to see the signs and carry out best practices when it comes to data security.
For example, your organization can create and provide self-service tools that enable every business unit to understand data privacy compliance. These can be things like data security exercise modules that take the user through company policy and ensure they understand each section before moving on to the next.
With 43% of employees admitting that they are “very” or “pretty” certain they have made a mistake at work with security ramifications, you must put time aside for this fundamental training.
4. Data security policies
Another way to nurture your team’s general data security practices is to create a clear data security policy. A data security policy outlines details about how customer data, employee PII (Personally Identifiable Information), and other sensitive information should be handled.
By adding the organization’s data security policy to the staff handbook and providing a summarized version that is easily accessible, the risk of a team member guessing at how they should proceed, getting it wrong, and potentially putting sensitive information at risk is reduced.
5. Run data breach simulations regularly
To mitigate potential data breaches, regularly conduct assessments of your cyber security, where either your in-house IT team or independent consultants will simulate a cyber-attack to detect any weaknesses in your organization’s security.
These penetration test simulations include technical attempts to break into your organization’s network by identifying and exploiting vulnerabilities, and social tests (e.g., phishing) that try to deceive your team into granting someone pretending to be an authority access that they shouldn’t have.
These kinds of tests mean you can find and remedy any weaknesses before a real attacker can exploit them.
6. Learn from mistakes
Even with secure systems in place, data breaches can still happen, and they must be reported within the statutory timeframe. In the EU, under the General Data Protection Regulation (GDPR), companies have a responsibility to report data breaches within 72 hours to the relevant authority, and there are similar protocols across the US. GDPR compliance software can be immensely helpful in keeping up with this responsibility.
Because of the importance of data breach reporting, it is critical that businesses respond quickly when a breach takes place by making use of a centralized and organized system. If the worst does happen, your business could use data breach software such as a data breach reporting assistant to help navigate this.
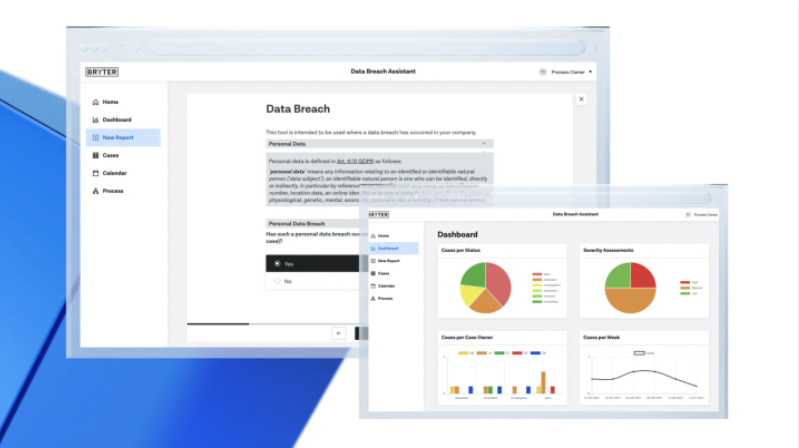
This type of software can also flag certain risks, provide insights into future best practices, and offer metrics on overall data breach risk reduction. This way, despite the financial or reputation losses from a data breach, your organization gains valuable lessons for the future to rebuild and understand how to prevent a data breach from happening again.
7. Vigilance
Lastly, it is imperative that you and your team remain vigilant against cybercriminals, who are constantly trying new tactics to access sensitive data. To reflect this, you should ensure that you are constantly looking for new ways to protect your organization’s data privacy and security.
Adopt these data privacy best practices in your organization
Most of these preventative measures can only work to the best of their capabilities with ongoing review and updates, and by keeping data secure automatically whenever possible. By regularly reviewing these data security processes, you can ensure that you remain ahead of breaches and diminish risk.
Learn how the no-code platformBRYTER can help your organization prevent breaches with educational tools, and manage breaches with data breach reporting software: sign up for a demo with our experts today. Or if you’d like to know how you can streamline your services, check out our guides to Workflow Automation.











